Have been struggling with LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj]
LNK:FakeFolder-B[Trj and Win32:Downloader-IWT [Trj] are two tricky computer threats specifically crafted to allow remote hacker to manipulate the target system and steal confidential information for further identity theft, commercial deceit, cyber attack and so on.
Except for the potential threats it may cause to the computer and end users, another reason why this malware raises complaints is its stubbornness when it comes to the removal. You must have been struggling with LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj] or hope to get far away with such infection when you are googling this backdoor Trojan. Read more then.
Both LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj] can open a backdoor to outside threat, and then trigger unwanted applications and programs installed on the computers. Those two threats get inside the poor protection computer quietly. It is usually packaged with freeware that users can download free from the internet. If you visit some malware sites, click any pop-up links or ads, or open unknown resource spam email attachments, LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj]can come up.
By build a bridge to connect cyber crooks who want to hack the poor protection computers into the system, LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj] might be terrible threats for computers. Hackers can use the special tech to filch system data and users’ personal privacy data without leaking traces by using the threat LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj].
Harmful Features of LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj]
1. Modify the settings of the system in the background.
2. Add new files and registry or other features which will attack the PC seriously.
3. Show many annoying pop-ups and redirections if you open your internet browsers to search something.
4. Drop other infections on the target computers.
5. Help hackers to steal your personal information such as usernames and passwords, or other valuable pieces of information.
Solutions to Remove LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj]
Step 1: Reboot your computer in safe mode with networking.
For Windows 8:
a. Press the Power button at the Windows login screen or in the Settings charm. Then, press and hold the” Shift” key on your keyboard and click Restart.
b. Click on Troubleshoot and choose Advanced Options. Then click on Startup Settings and select Restart. Your PC will restart and display nine startup settings. Now you can select Enable Safe Mode with Networking.

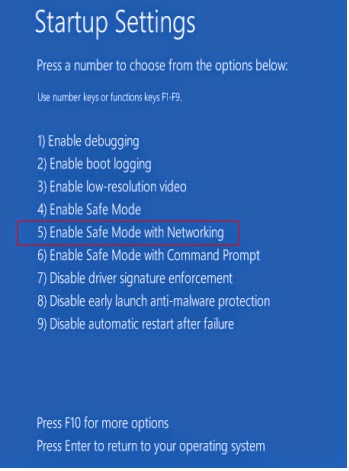
For Windows 7/Vista/XP:
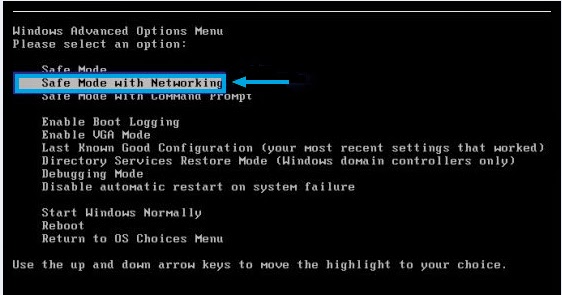
a. Restart the computer. Before Windows Welcome interface appears, please tap F8 key constantly until Windows Advanced Options Menu displays.
b. On the black screen of Windows Advanced Options Menu, use the arrow key to move down and choose Safe Mode with networking option by highlighting it. Then hit Enter on the Keyboard.
Step 2: End the processes related to the LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj] in Windows Task Manager.
For Windows 8 users:
Right-click the taskbar and select “Task Manager”. Click “More details” button when you see the Task Manager box. After that, hit “Details” tab to find out the processes of the Trojan and then hit the End task button.
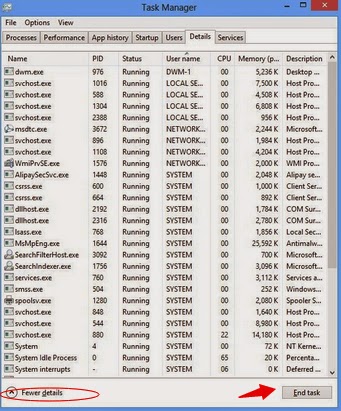
For Windows 7/Vista/XP users:
Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab, find out the related processes, and end up of them.
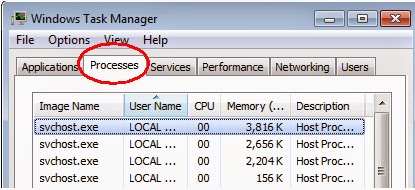
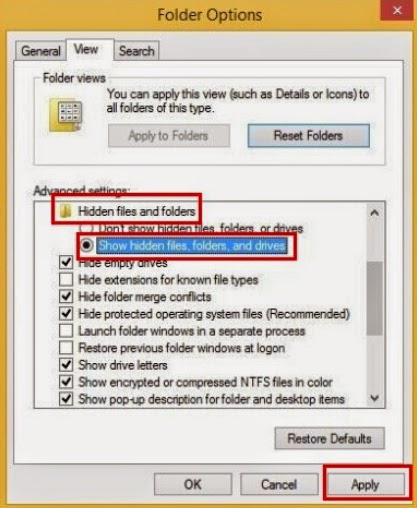
Step 3: Show hidden files and folders.
Windows 7/Vista/XP users:
1). Click on Start button and then on Control Panel
2). Click on Appearance and Personalization
3). Click on Folder Options
4). Click on the View tab in the Folder Options window
5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
6). Click OK at the bottom of the Folder Options window
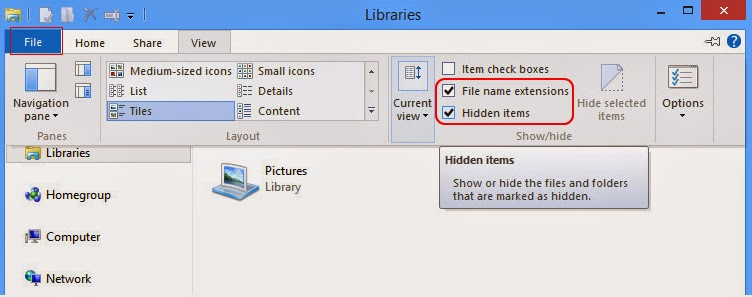
Windows 8 users:
Open Windows Explorer from the Start screen. Click View tab. Tick “File name extensions” and “Hidden items” options and then press OK to show all hidden items.
Step 4: Scanning your computer by using removal software.
Clicking the download below to download SpyHunter.
How to Install SpyHunter: On the ground of these tips, get to know how to how to install SpyHunter malware scanner on your operating system:
1. Execute the installation process by double-clicking the downloaded file.
2. Follow the prompts to finish the installation of SpyHunter.
3. After the installation has been successfully completed, please start a full scan with your PC.
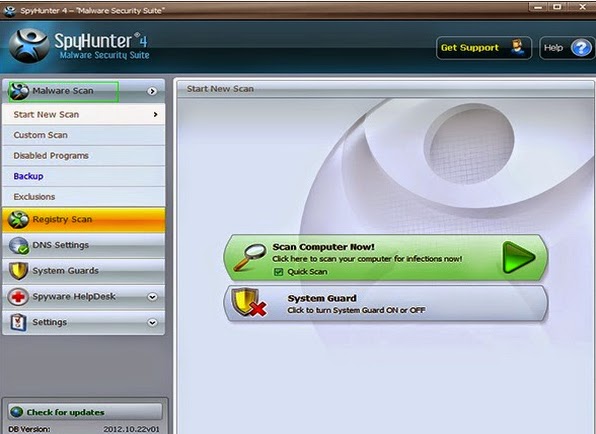
4. Remove all detected infections after scanning.
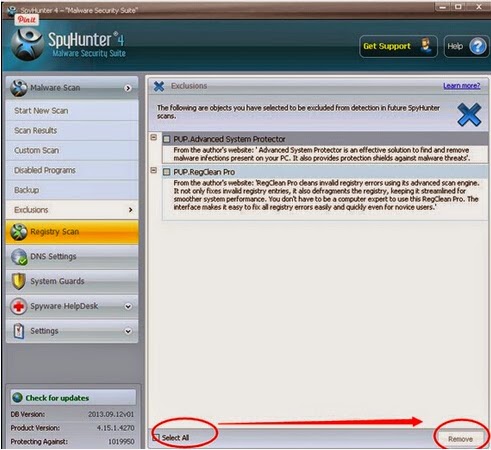
Optional guide:
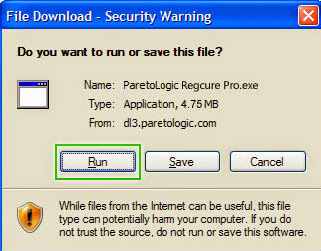
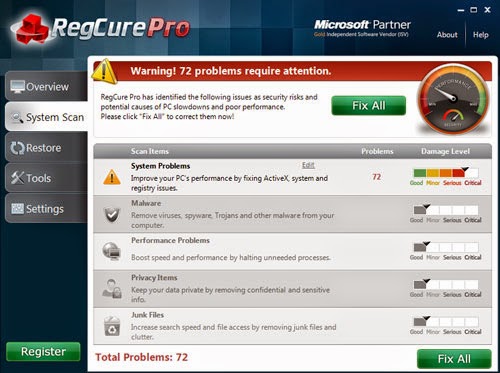
You can choose run RegCure Pro to check your computer again.The following steps will step by step to tell you download and install it on your computers.
1.Click here to download RegCure Pro



Quick Notice: LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj] do a great deal of behaviors on the infected system, to make sure your computer safe, you are asked to remove thoese threats from your PC.Manual steps are complex and difficult, if you are not a professional tech, please don’t delete any host file. We here recommend you removing LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj] with popular and useful removal tool.
>> Download LNK:FakeFolder-B[Trj] and Win32:Downloader-IWT [Trj] Removal Tool Here!
No comments:
Post a Comment