Sophisticated and Persistent Poweliks Malware
Poweliks is known as a type of malware that can do a lot of things on the infected computers. It is also detected as a type of Trojan by some security products like Symantec and Norton. In form of Trojan, it has a new name called Trojan.Poweliks or Powerlik. This a new potential nasty infection that is a typical Trojan that can target all mainly use of the system of Windows such as Windows Xp, Windows 2000, Windows Vista, Windows 7 and Windows 8.
Poweliks(Powerlik) or Trojan.Poweliks creates new files and registries which can cause a system file missing or crashing. It can attempt to evade detection and analysis by running entirely from the system registry without creating files on disk, security researchers warn. In addition, it adds new features like many unknown shortcuts, icons or background which are totally different from your previous computer.
Poweliks is difficult to be removed from Windows. For it spreads via emails through a malicious Microsoft Word document and then inserts an encoded registry key and to remain undetectable it keeps the registry key hidden, so you cannot search the files and registry which make the removal processes turn into hard work. Trojan.Poweliks may open a backdoor to outside threats, so your system may be easy to get infected with many other malware ,browser hijacker, adware such as wxdownload Ads, Astro Arcade, PWS:win32/Zbot.gen!AP, WSE_Astromenda. What is more, Poweliks record the important information like browsing history and online input date and privacy data such as bank account or logon account details. In addition, this malware tries to connect to‘hard coded IP addresses’in an effort to receive further commands from the attacker. So you have to remove Poweliks or Trojan.Poweliks from your PC as soon as possible you can.
What Poweliks or Trojan.Poweliks Actually Do on Your PC?
A, this Trojan can run into the comprised system without user’s consent.
B, this malware can create new files and registry, and change the settings of the internet browsers.
C, you will be redirected to malware sites and get a lot of pop up ads.
D, it can open a backdoor to other malware, worm, or other infections.
E, this infection is created to help hackers to steal user important data, record visiting habits and so on and then they can use onto the marketing purpose.
Three Branches to Remove Poweliks (Trojan.Poweliks)
Step 1: Reboot your computer in safe mode with networking.
For Windows 8:
a. Press the Power button at the Windows login screen or in the Settings charm. Then, press and hold the” Shift” key on your keyboard and click Restart.
b. Click on Troubleshoot and choose Advanced Options. Then click on Startup Settings and select Restart. Your PC will restart and display nine startup settings. Now you can select Enable Safe Mode with Networking.

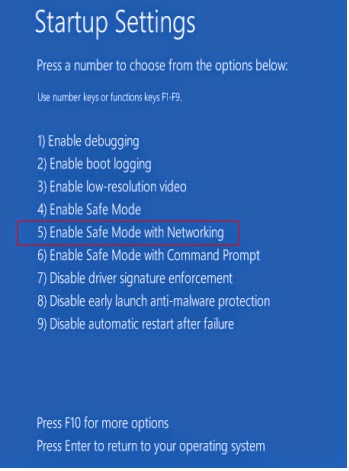
For Windows 7/Vista/XP:
a. Restart the computer. Before Windows Welcome interface appears, please tap F8 key constantly until Windows Advanced Options Menu displays.
b. On the black screen of Windows Advanced Options Menu, use the arrow key to move down and choose Safe Mode with networking option by highlighting it. Then hit Enter on the Keyboard.
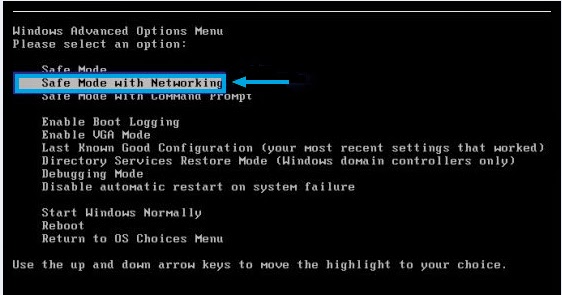
Step 2: End the processes related to Poweliks in Windows Task Manager.
For Windows 8 users:
Right-click the taskbar and select “Task Manager”. Click “More details” button when you see the Task Manager box. After that, hit “Details” tab to find out the processes of the Trojan and then hit the End task button.
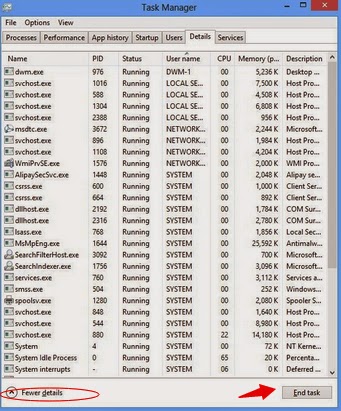
For Windows 7/Vista/XP users:
Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab, find out the related processes, and end up of them.
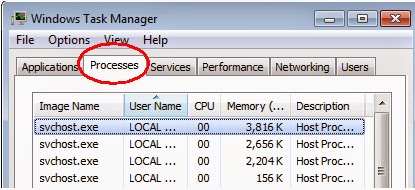
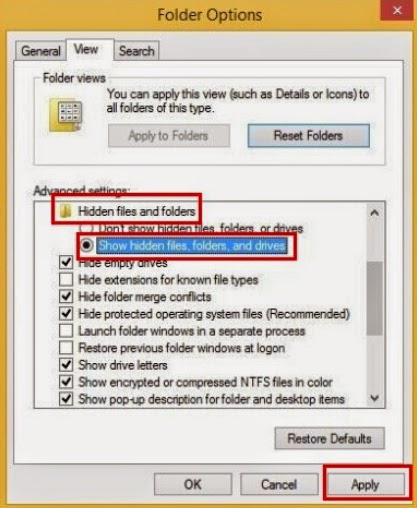
Step 3: Show hidden files and folders.
Windows 7/Vista/XP users:
1). Click on Start button and then on Control Panel
2). Click on Appearance and Personalization
3). Click on Folder Options
4). Click on the View tab in the Folder Options window
5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
6). Click OK at the bottom of the Folder Options window
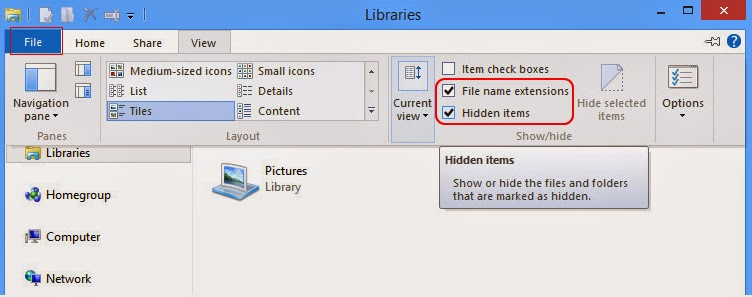
Windows 8 users:
Open Windows Explorer from the Start screen. Click View tab. Tick “File name extensions” and “Hidden items” options and then press OK to show all hidden items.
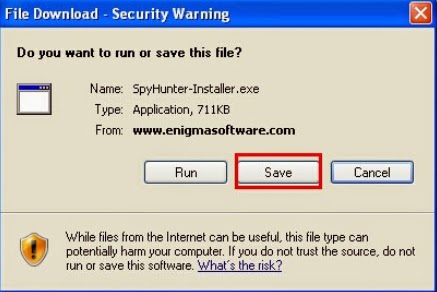
Step 4: Scanning your computer by using removal software.
Clicking the download below to download SpyHunter.
How to Install SpyHunter: On the ground of these tips, get to know how to how to install SpyHunter malware scanner on your operating system:
1. Execute the installation process by double-clicking the downloaded file.
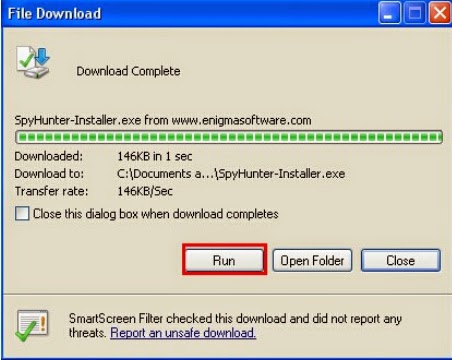
2. Follow the prompts to finish the installation of SpyHunter.
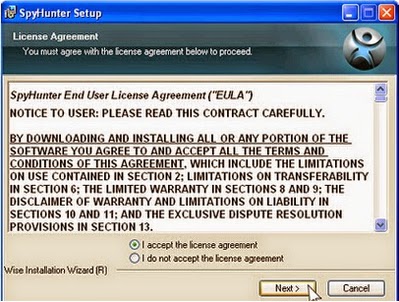
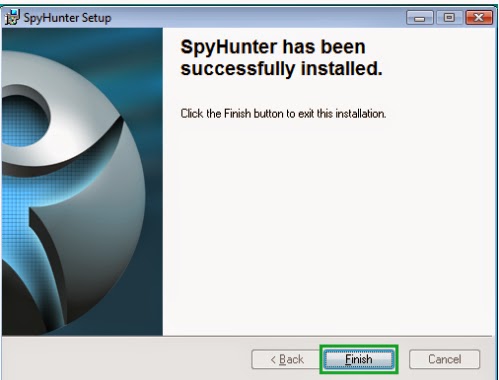
3. After the installation has been successfully completed, please start a full scan with your PC.
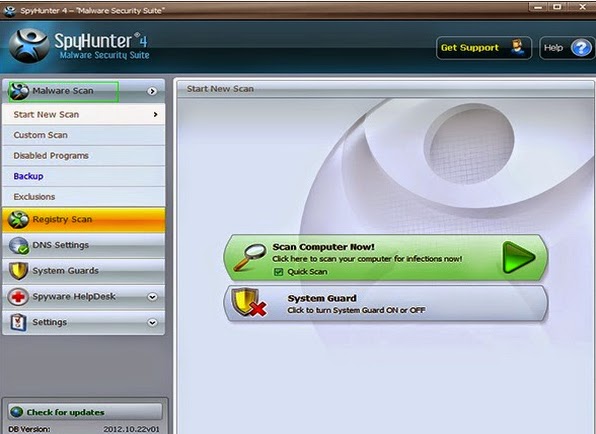
4. Remove all detected infections after scanning.
Warning Tip:
Poweliks is tricky malware that is a typical Trojan that can do many dangerous activities on the installed computers. As soon as this malware comes out, you may get a lot of pop-up warnings, and redirections to malware sites. And some other malware or threats can be installed on your system, so you have to remove Poweliks or Trojan.Poweliks with powerful and reliable removal tool here.
No comments:
Post a Comment