Are You still Fighting with Angler Exploit Virus?
Angler Exploit virus is so pesky that you might be annoyed by its activities. Once installed, this virus starts to do a list of activities on the installed PC. And then you might notice its appearance by the following signs;
> Computer would stuck at multiple tasks and run much slowly than before;
> Page loading speed is much slower and the Internet connectivity is somehow unstable;
> Ads may start to popup when you are browsing and they will increase in frequency;
> Useless add-ons, extensions and toolbar application will come in your sight;
> Wanted results may back to you if you hit back again;
> Certain sites may be blocked and your homepage will not be changed back no matter what you have tried.
Angler Exploit virus conceals itself under some host files in the background without you knowing. Then it will install in svchost.exe process in order to drop down and execute additional files bundle with Installation.exe. It can connect to some websites associated to malware for downloading and installing more malicious files on the attacked system. Meanwhile, Angler Exploit virus always returns again every time your computer starts, your browser is redirected to random sites.
How Angler Exploit Virus Gets into Your PC?
Angler Exploit virus sneaks into the system without your notification, and it often seeks thousands of ways to spread to the computers. It usually infiltrates the computer through other infection. Security holes and software vulnerabilities on the computer can also be exploited by an attacker to drop Angler Exploit virus. If your computer has any system loophole or security fragility, it can catch a chance to infect your computer. Besides, if you are an innocent computer user, and click any spam email attachments, open any malware site, download freeware which has been bundled with this infection, or abnormal surfing activities, Angler Exploit virus might install on your computer slightly.
Removal Steps to Get Rid of Angler Exploit Virus Completely
Step A: Restart your computer and enter into safe mode with networking.
Windows 8 users:
a. Press the Power button at the Windows login screen or in the Settings charm. Then, press and hold the” Shift” key on your keyboard and click Restart.
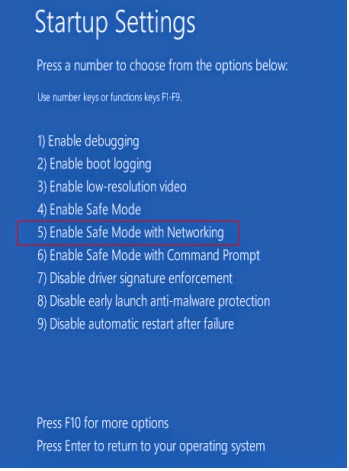
b. Click on Troubleshoot and choose Advanced Options. Then click on Startup Settings and select Restart. Your PC will restart and display nine startup settings. Now you can select Enable Safe Mode with Networking.

Windows 7/Vista/XP users:
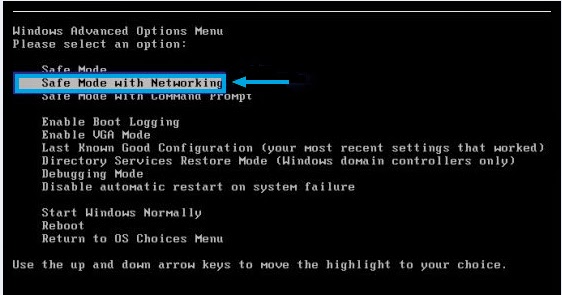
a. Restart the computer. Before Windows Welcome interface appears, please tap F8key constantly until Windows Advanced Options Menu displays.
b. On the black screen of Windows Advanced Options Menu, use the arrow key to move down and choose Safe Mode option by highlighting it. Then hit Enter on the Keyboard.
Step B: Show hidden files and folders.
Windows 8:
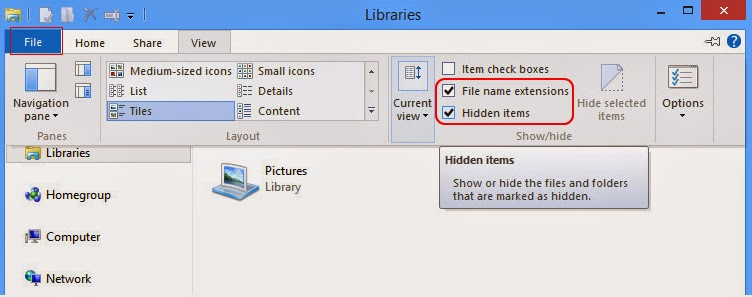
Open Windows Explorer from the Start screen. Click View tab. Tick “File name extensions” and “Hidden items” options and then press OK to show all hidden items.
Windows 7/Vista/XP:
(1). Click on the Start button and then on Control Panel
(2). Click on the Appearance and Personalization link
(3). Click on the Folder Options link
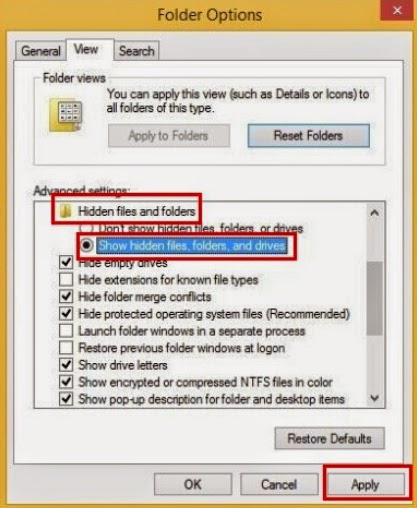
(4). Click on the View tab in the Folder Options window
(5). Choose the Show hidden files, folders, and drives under the Hidden files and folders category
(6). Click OK at the bottom of the Folder Options window.
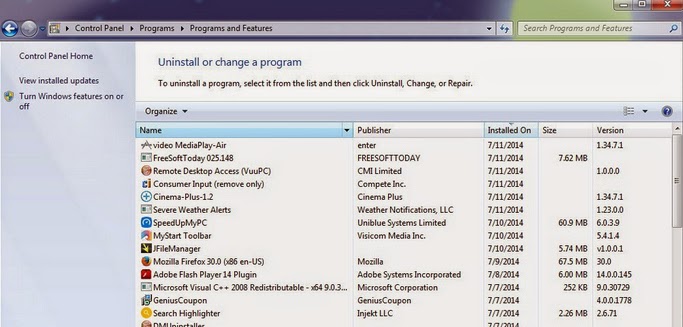
Step C: Delete unwanted software
Win8 users:
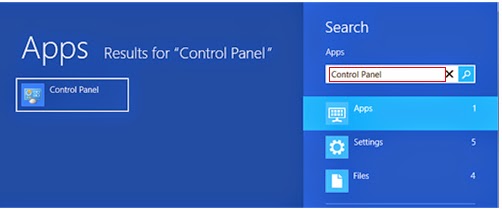
1. Press Win+R, type in “control” and tap Enter
2. Select Uninstall a program/Add or remove programs
3. Highlight the unwanted application
4. Click Uninstall/Remove
Windows 7 & Vista users:
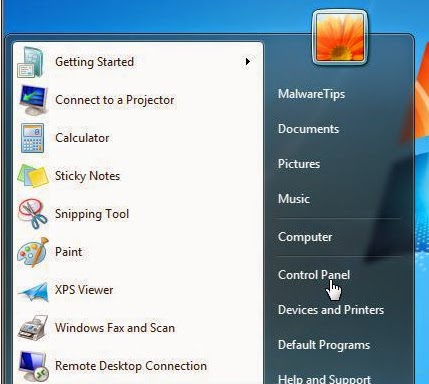
• From the Start Menu, select Control Panel.
• Under Programs click the Uninstall a Program link.
• Select the program you wish to remove and right click then select Uninstall/Change.
• Follow the prompts to finish the uninstallation of the software.
Windows XP users:
• From the Start Menu, select Control Panel.
• Click the Add or Remove Programs icon.
• Select the program you wish to remove and right click then select Uninstall/Change.
• Follow the prompts to finish the uninstallation of the software.

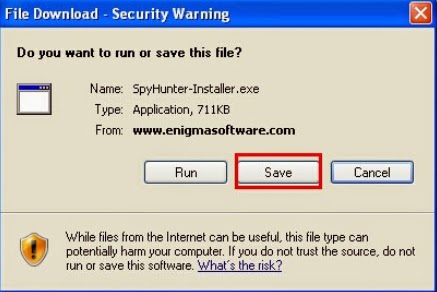
Step D: Download SpyHunter's Malware Scanner to Detect and Remove Angler Exploit Virus.
1: Click download button below to download SpyHunter.2: You just need to follow the installation prompts on your screen and don’t make any change during the installing procedure.
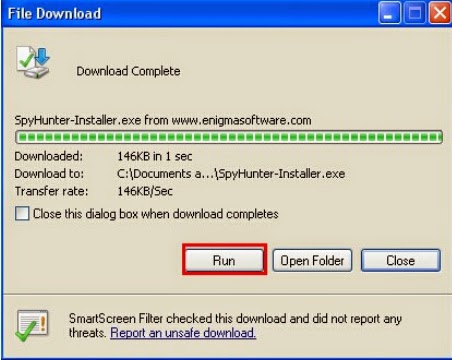
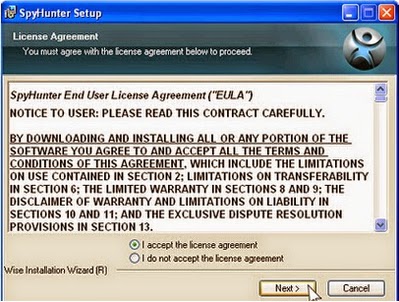
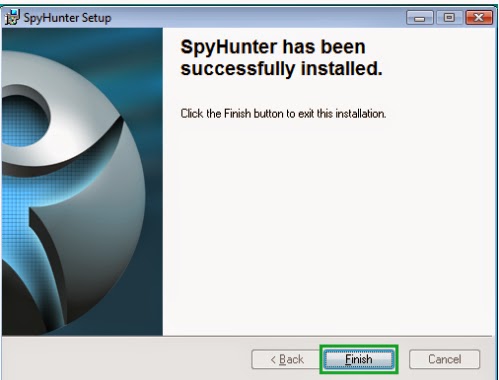
3: If you have installed SpyHunter successfully, please SCAN your computer by clicking MALWARE SCAN or SCAN NOW button.
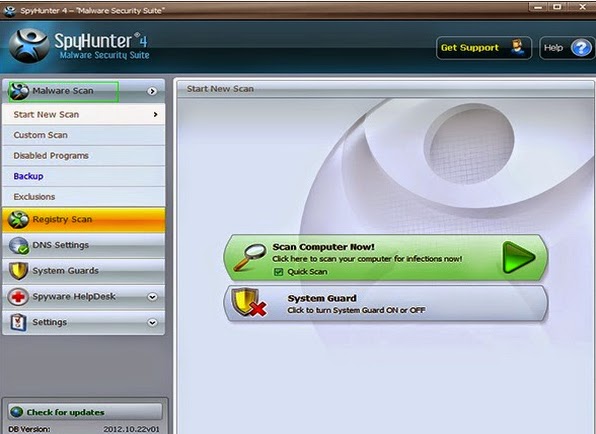
4: Once scan completes, please remove all noted infected files.
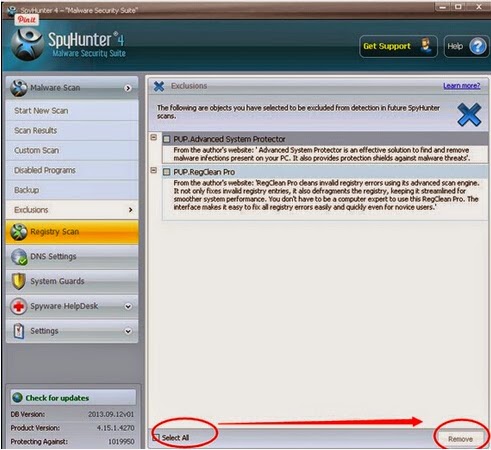
Step E: Restart your computer back to the regular mode to check the changes.
Double Check with RegCure Pro
After the scanning with SpyHunter, to make sure your computer safe, please check it with RegCure Pro again.
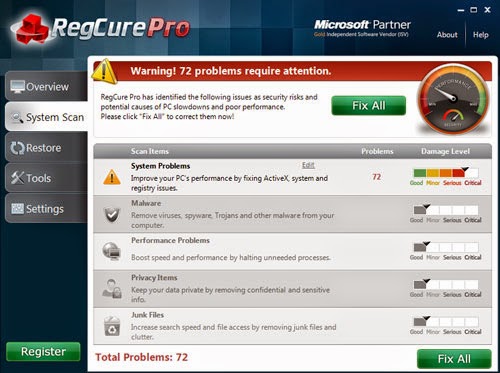
RegCure Pro is a tool to fix the common problems that cause PCs to become slow, sluggish and erratic performers. This software is a fantastic cleaner. It gets rid of active malware and viruses, registry errors, junk files, unneeded process and programs that slow your PC down and make for long startup times.
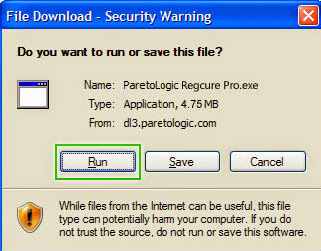
1.Click here to download RegCure Pro

1) You will need to click Save or Run to install the application. (If you choose to save the application, we recommend that you save it to your desktop and initiate the free scan using the desktop icon.
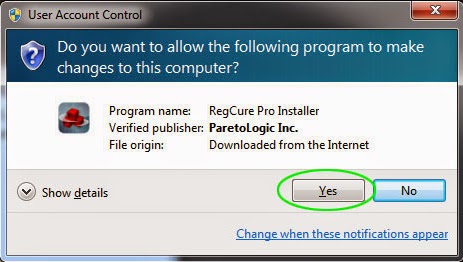
2) Once the file has downloaded, give permission for the Setup Wizard to launch by clicking the "Next" button. Continue following the Setup Wizard to complete the RegCure Pro installation process.

2. Click “Start Scan” to do a scan with your system.

3. Delete all detected issues and fix PC with RegCure Pro.
Be aware: If you desire to try Angler Exploit virus manual elimination, in order to avoid the damage or loss of precious data, you should be mindful to backup Windows registry first before performing the removal approach. In case, if you don’t know much about knowledge about computer, please try to use easiest and complete removal guide–using famous removal tool.
Free Download Scanner to Detect Angler Exploit Virus
BEST WAY TO KEEP PC SAFE AND PROTECT AGAINST UPCOMING THREATS WITH SPYHUNTER
No comments:
Post a Comment