Once Exploit:Java/CVE-2012-0507 installed on my laptop, there are some unexpected issues have appeared on my system;
ISSUES:
1) Adverts and hyperlinks inserted all over webpage
2) Browser hijacked by some malicious websites.
3) Regular browser redirects to several different links
4) Laptop is running very slow
5) My email has become pretty much unresponsive.
6) Some other unknown programs installed on my system slightly.
How do I fix all issues caused by Exploit:Java/CVE-2012-0507? Will someone help me?
Stubborn and Funky Exploit:Java/CVE-2012-0507
Exploit:Java/CVE-2012-0507 is usually classified as a type of Trojan virus that can attack the infected computers seriously and bring many damages onto the system. It can add new codes and change locations, that antivirus may really never remove it completely. With more and more things break into your computer and take place the limited resource of your system.
The performance of your computer will obviously turn slow. And this Trojan can be regard as a backdoor to infections outside, after getting infected with Exploit:Java/CVE-2012-0507, a bunch of stuff like Trojan, worm, adware, browser hijacker or malware may be installed on the infected computers.
Exploit:Java/CVE-2012-0507 seems be able to make changes of the web browsers, and then causes a lot of annoyances when you are using them. Adverts and hyperlinks inserted all over webpage which you are browsing, and you also get many annoying redirects to some unknown and malware sites freely once you open new links. What is more, Exploit:Java/CVE-2012-0507 allows cyber criminals to get into the system without taking much time and they steal very important confidential and sensitive information.
Means 1: Remove Exploit:Java/CVE-2012-0507 Manually
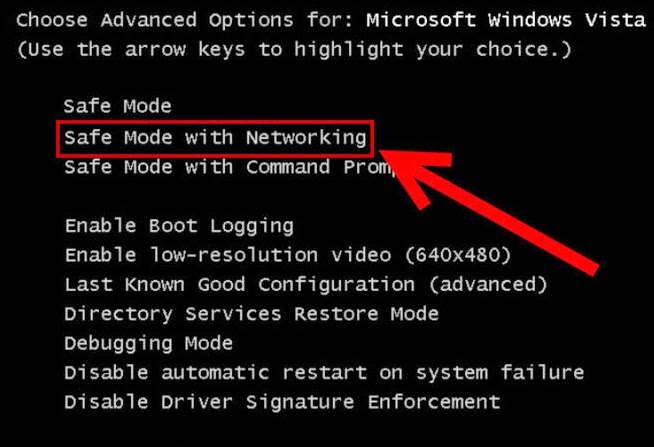
STEP 1 Reboot your computer in safe mode with networking.
For Windows 8:
Press the Power button at the Windows login screen or in the Settings charm. Then, press and hold the” Shift” key on your keyboard and click Restart.
Click on Troubleshoot and choose Advanced Options. Then click on Startup Settings and select Restart. Your PC will restart and display nine startup settings. Now you can select Enable Safe Mode with Networking.


Windows 7/Vista/XP:
Reboot your PC and then log on Safe mode with networking.
Restart your computer; Press F8 key before the window launches; Choose Safe mode with network option.
STEP 2 End the processes related to Exploit:Java/CVE-2012-0507 in Windows Task Manager.
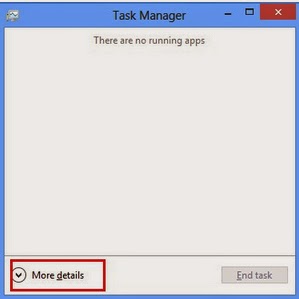
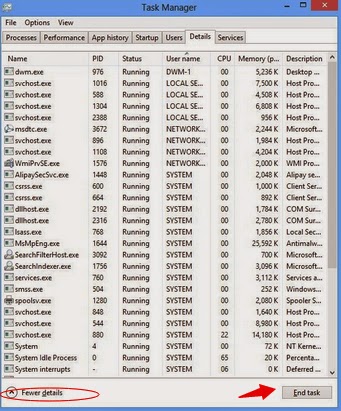
Windows 8:
Right-click the taskbar and select “Task Manager”. Click “More details” button when you see the Task Manager box. After that, hit “Details” tab to find out the processes of the Trojan and then hit the End task button.
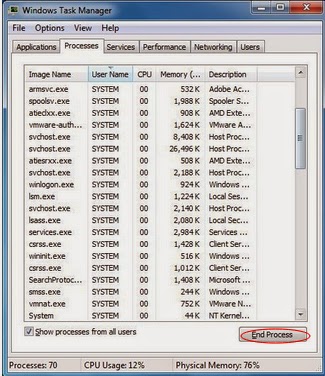
Windows 7/Vista/XP:
To stop all related processes, press CTRL+ALT+DEL to open the Windows Task Manager. Click on the “Processes” tab, search related processes and then right-click it and select “End Process” key
STEP 3 Uninstall any dubious PUP from computer
For Windows 7/Vista: Click “Start” (“Windows Logo”)>”Control Panel“>”Uninstall a program“(under Program)>look for any dubious programs, select them and click Uninstall/Change.
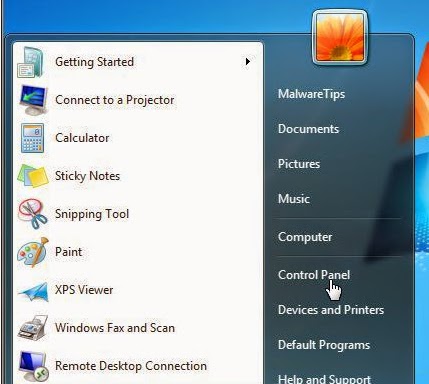
For Windows 8: Right-click on the screen’s bottom-left corner> “Control Panel” >”Uninstall a program“(under Program)> Look for any dubious programs, select them and click Uninstall/Change.

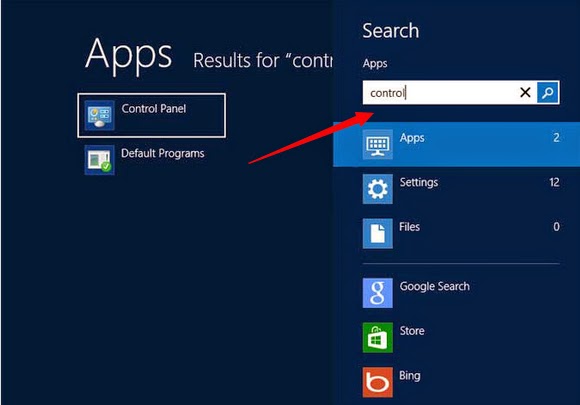
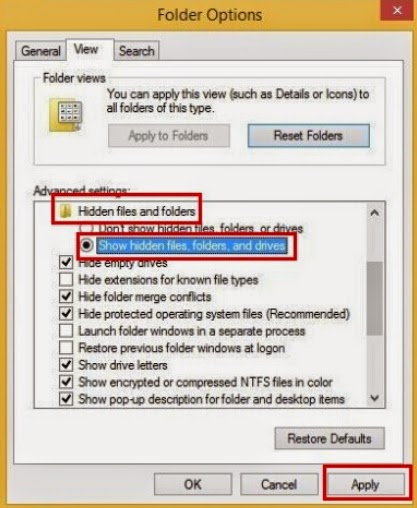
STEP 4 Show hidden files and folders.
Windows 8:
Open Windows Explorer from the Start screen. Click View tab. Tick “File name extensions” and “Hidden items” options and then press OK to show all hidden items.
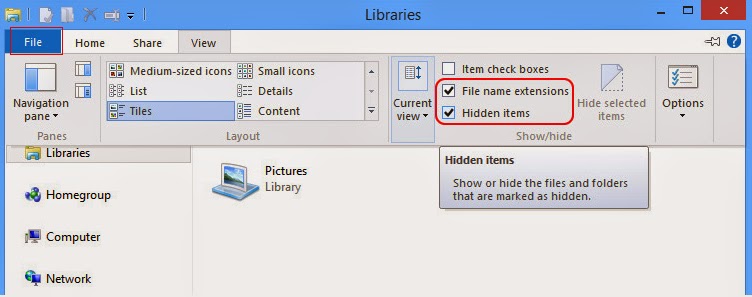
Windows 7/Vista/XP:
1. Close all programs so that you are at your desktop.
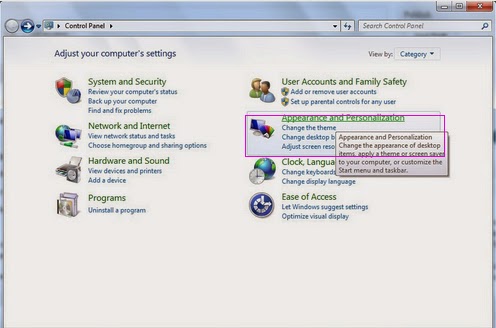
2. Click on the Start button. This is the small round button with the Windows flag in the lower left corner. 3. Click on the Control Panel menu option.
4. When the control panel opens click on the Appearance and Personalization link.
5. Under the Folder Options category, click on Show Hidden Files or Folders.
6. Under the Hidden files and folders section select the radio button labeled Show hidden files, folders, or drives.
7. Remove the checkmark from the checkbox labeled Hide extensions for known file types.
8. Remove the checkmark from the checkbox labeled Hide protected operating system files (Recommended).
9. Press the Apply button and then the OK button.
STEP 5 Find out and delete associated files of Exploit:Java/CVE-2012-0507 listed below:
%UserProfile%\Application Data\Microsoft\[random].exe
%User Profile%\Local Settings\Temp
%Documents and Settings%\All Users\Start Menu\Programs\[Bad Image]
%Documents and Settings%\All Users\Application Data\[ Bad Image]
%Program Files%\[ Bad Image]
STEP 6 Find out and remove the registry entries as below:
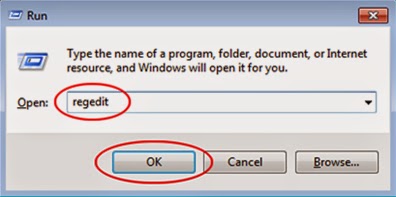
Windows 7/Vista/XP:
Step: Hold down the Windows key on your keyboard and press the "R" button. Type in "regedit" and hit "Enter" to gain access to the Registry Editor.

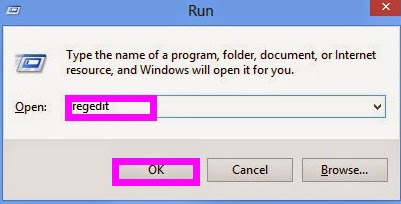
If you are Windows 8 users:
Press Windows Key+R, go to run, then type “regedit” in the box to open Registry Editor, after that, and then find out the registry entries below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Current Version\Uninstall\[Bad Image]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
Means 2: Remove Exploit:Java/CVE-2012-0507 Automatically
1. Download Removal Tool Here!
2. Installing the tool on your system by following the quick menu of the prompts on the Windows.
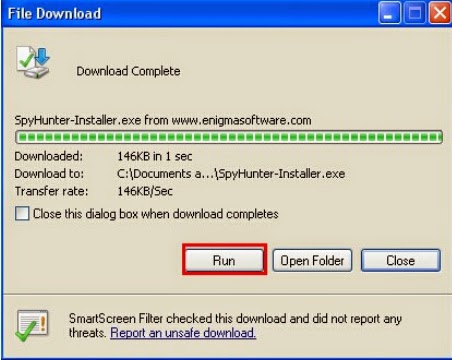
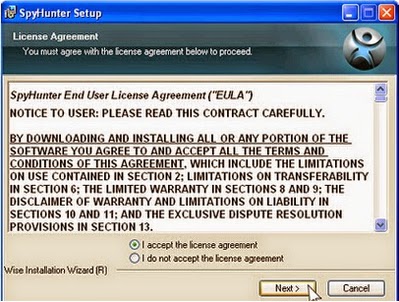
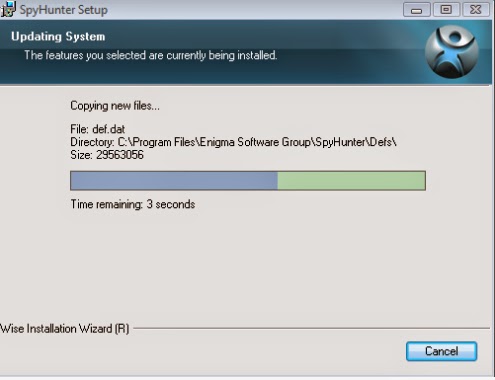
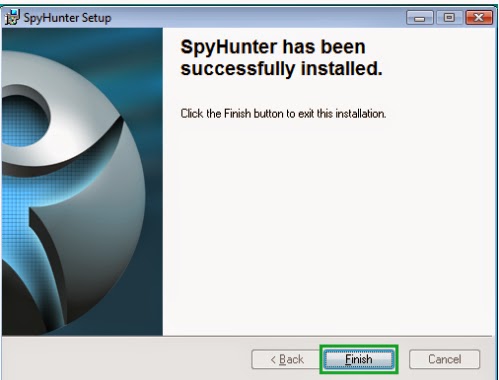
3. Start a full scan on your PC to detect and pick up this infection and related add-ons.
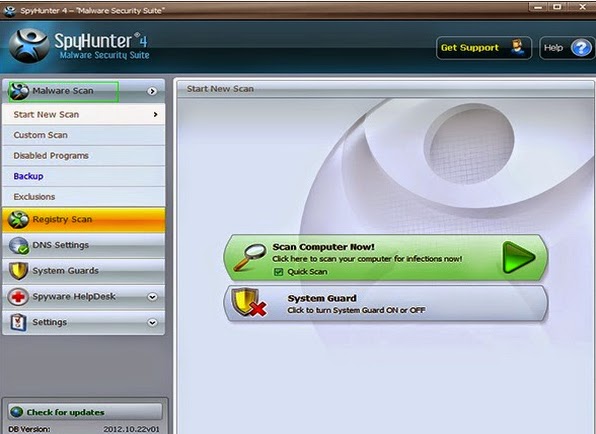
4. Click remove button to clear up all infected files.
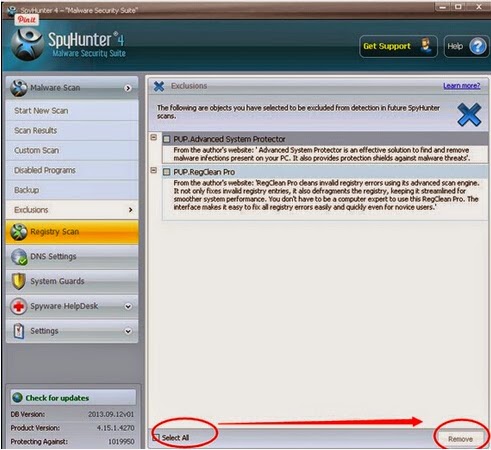
Optional step: After removing Exploit:Java/CVE-2012-0507 , you can use Perfect Uninstaller removed all unneeded applications, empty registry files on your PC. Remove programs that could not be removed by Add/Remove Programs make your system runs smoothly.
Perfect Uninstaller is a better and easier way for you to completely and safely uninstall any unneeded or corrupt application that standard Windows Add/Remove applet can't remove. If your are trouble with uninstalling unwanted application software in your computer and seeking for a perfect solution. You can click this link to download Perfect Uninstaller.
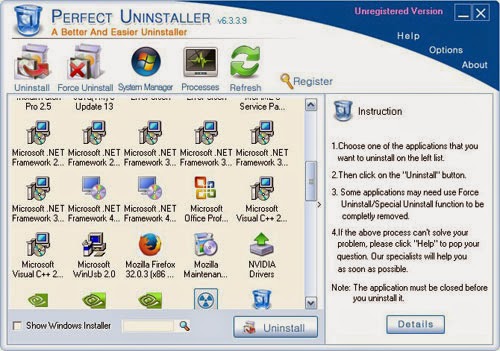
Feartures And Benefits of Perfect Uninstaller
• Easily and completely uninstall programs
• Completely clean the empty / corrupted registry entries
• Forcibly uninstall any corrupted programs
• Forcibly display and uninstall hidden programs
• Much faster than the Add/Remove applet.
• Easy to use with friendly user interface.
• System Manager.
• Operating System: Windows 95/98/ME/NT/2000/2003/XP/ Vista32/ Vista64

How to download and install Perfect Uninstaller on PC.
Step 1: Click below icon to download Perfect Uninstaller
Step 2: To install the software just double click the PerfectUninstaller_Setup.exe file.

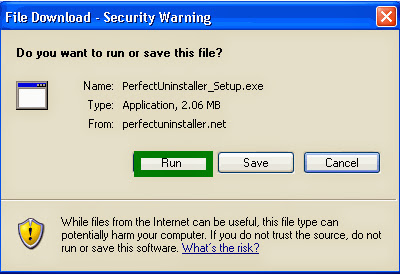
Step 3: Select "Run" to download and install Perfect Uninstaller. (If you prefer you may save the Perfect Uninstaller setup file (PerfectUninstaller_Setup.exe) to your computer and install the software later by clicking on the 'Save' button.)
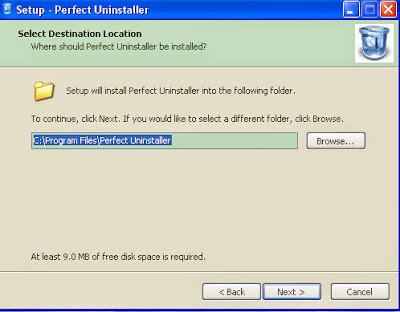
Step 4: The next screen will ask for a "Destination Folder".
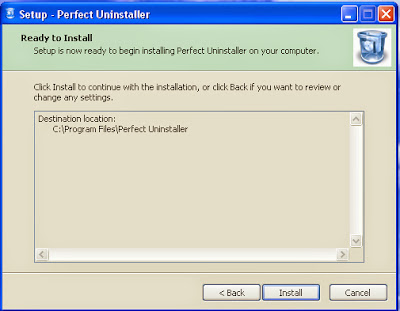
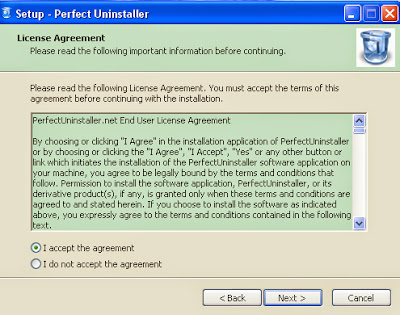
Step 5: Once the file has downloaded, give permission for the Setup Wizard to launch by clicking the "Next"button. Continue following the Setup Wizard to complete the Perfect Uninstaller installation process by click "Finish.".
After installation, you can follow the steps below to uninstall unwanted programs:
1: Right click the folder to select “Force Uninstall”.
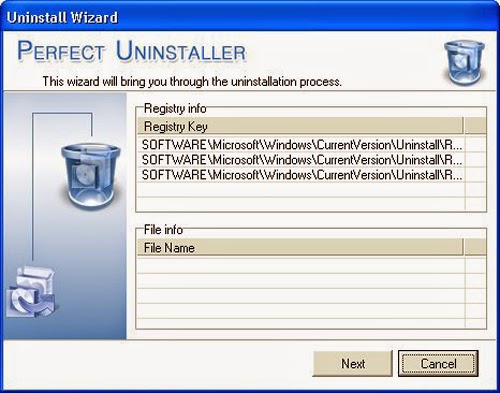
2: Perfect Uninstaller will run as below, click “Next” to proceed.
3: Perfect Uninstaller is scanning your PC for associated entries. Click “Next” to remove them.
4: Follow the on-screen steps to finish the uninstall process.
Kindly Notification:
To kick out of Exploit:Java/CVE-2012-0507 from your system, you should master good computer knowledge, for the removal process is related with host files and registry, if you make any mistake, it will cause system crash and files missing. You are welcoming to download best removal tool here to remove Exploit:Java/CVE-2012-0507 completely.
No comments:
Post a Comment