The Means Used by TR/FakeAV.1170432.5 To Reach Your PC
TR/FakeAV.1170432.5 gets to the computer surreptitiously, it can target computer via visiting explicit and other compromised web sites, clicking any email attachment, or opening any pop up advertisement or link. Drive-by download or files sharing also the main ways to spread this threat. Another common way is used by this TR/FakeAV.1170432.5 bypassing the existing security tools including Windows Firewall.
The side effect of TR/FakeAV.1170432.5
After TR/FakeAV.1170432.5 installing, you usually find this threat on db21.exe or any other files of the computers. This is a typical infection that can affect Windows 9x, 2000, XP, and Windows Vista/7/8. TR/FakeAV.1170432.5 tries to manipulate the settings which related to the booting of computers. Thus, some unfamiliar shortcuts, icons, even .exe or .dll files appear suddenly. And a bunch of unknown add-ons or programs added onto the computers which slow down your system performance.
TR/FakeAV.1170432.5 affects the existing processes and blocks some certain programs on the infected system like Windows Updates/Security Center are unavailable during this potential crisis. In addition, TR/FakeAV.1170432.5 will open a backdoor to propagate other outside threats such as rouge security software, worm, Trojan virus or other malicious applications and a ton of unwanted programs can be installed on your computer without your notification.
Two Lessons to Get Rid of TR/FakeAV.1170432.5 from Windows XP/ Vista/7/8
Lesson 1: TR/FakeAV.1170432.5 Manual Removal
Before you performing manual steps, please back up all your Windows registry and important files. For any mistake may cause loss of precious data.
Step one: Reboot your computer into Safe Mode with Networking
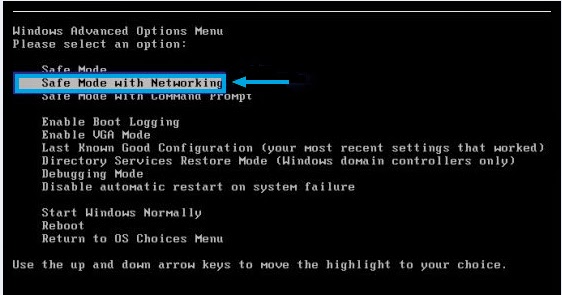
Windows XP/ Vista/7:
Turn your computer off and then back on and immediately when you see anything on the screen, start tapping the F8 key on your keyboard.
Using the arrow keys on your keyboard, select Safe Mode with Networking and press Enter on your keyboard.
For win8:
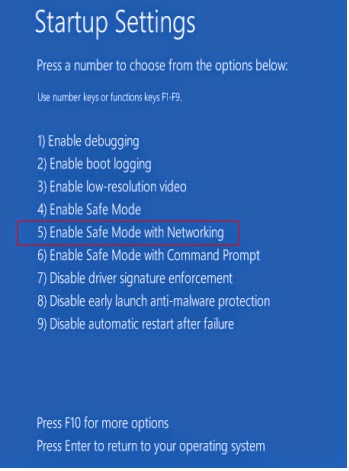
Reboot your computer in safe mode with networking.
Press the Power button at the Windows login screen or in the Settings charm. Then, press and hold the ” Shift” key on your keyboard and click Restart.
Click on Troubleshoot and choose Advanced Options. Then click on Startup Settings and select Restart. Your PC will restart and display nine startup settings. Now you can select Enable Safe Mode with Networking.

Step two: Show hidden files
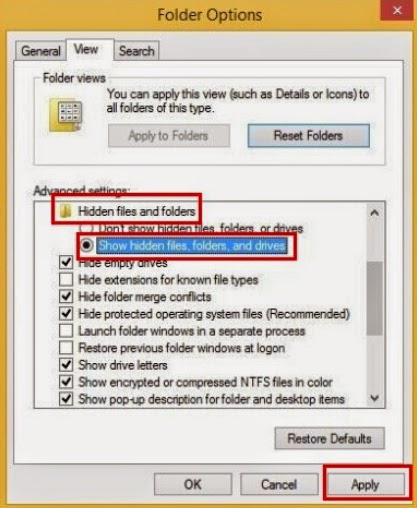
a) Open Control Panel from Start menu and search for Folder Options;
b) Under View tab to tick Show hidden files and folders and non-tick Hide protected operating system files (Recommended) and then click OK;
c) Click on the “Start” menu and then click on the “Search programs and files” box, Search for and delete these files generated by this Trojan:
%AppData%\[RANDOM CHARACTERS]\[RANDOM CHARACTERS].exe
%AllUsersProfile%
%AllUsersProfile%\Programs\{random letters}\
%AllUsersProfile%\Application Data\~r
%AllUsersProfile%\Application Data\~dll
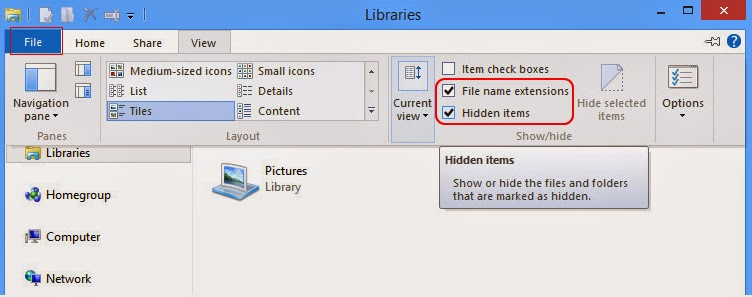
*For Windows 8 users
a. Open Windows Explorer from Start screen, navigate to View tab. At Show/Hide column, tick both file name extensions and Hidden items and hit Enter.
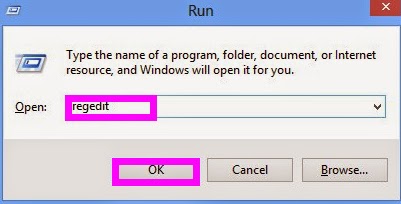
Step three. Examine following entries respectively. Seeing any suspicious key value started with Run, right click on it and select Delete.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Current Version
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders Startup=”C:\windows\start menu\programs\startup
Lesson 2: TR/FakeAV.1170432.5 Automatic Removal with Removal Tool
For manual removal of this infection needs to know more about special computer skills, if you have no more knowledge, please don’t do any trial.
1: Download Removal Tool by clicking the below icon. (if you feel your computer sluggish, please restart your PC and then sign in safe mode with networking.)
2: Installation process:
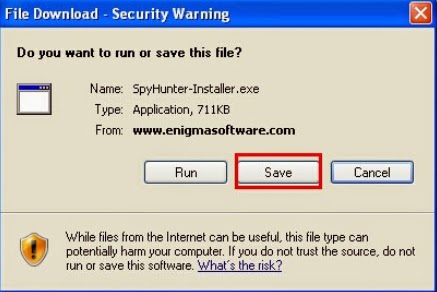
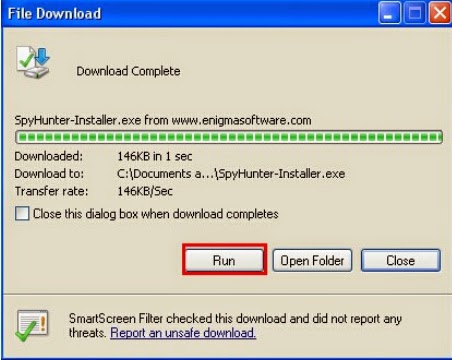
1) Check out the "File Download", and press "Save" to save SpyHunter file. “Save” the SpyHunter file on your Desktop.
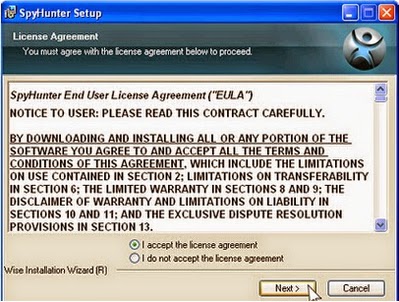
2) Double click on the installation file and you will be prompted with a license agreement. Please read through the license agreement and check the box stating that you agree to the terms and click "Next."
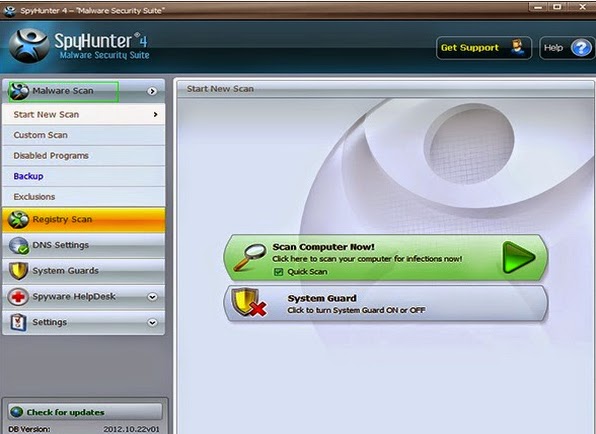
3: After the installation has been successfully completed, SpyHunter will start scanning your system automatically.
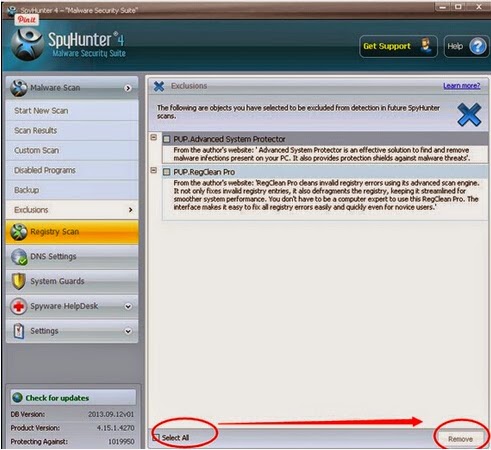
4: You should now click on the Remove button to remove all the listed malware.
Double Check with RegCure Pro
After the scanning with SpyHunter, to make sure your computer safe, please check it with RegCure Pro again.
RegCure Pro is a tool to fix the common problems that cause PCs to become slow, sluggish and erratic performers. This software is a fantastic cleaner. It gets rid of active malware and viruses, registry errors, junk files, unneeded process and programs that slow your PC down and make for long startup times.
1.Click here to download RegCure Pro

1) You will need to click Save or Run to install the application. (If you choose to save the application, we recommend that you save it to your desktop and initiate the free scan using the desktop icon.
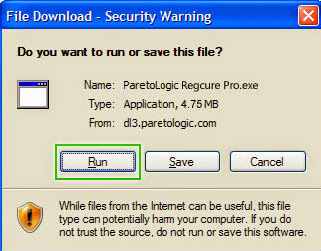
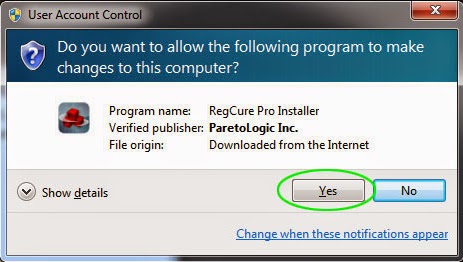
2) Once the file has downloaded, give permission for the Setup Wizard to launch by clicking the "Next" button. Continue following the Setup Wizard to complete the RegCure Pro installation process.

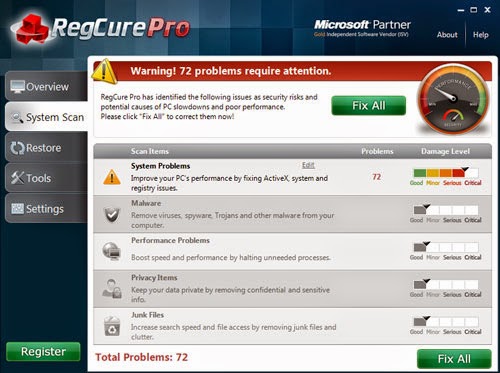
2. Click “Start Scan” to do a scan with your system.

3. Delete all detected issues and fix PC with RegCure Pro.
In Conclusion:
If you don’t know how to get rid of TR/FakeAV.1170432.5, you just need to download famous removal tool to remove TR/FakeAV.1170432.5 automatically.
No comments:
Post a Comment