Potential Threats Caused by A28.pieehk.com:
- Endless annoying pop-ups may display on any webpage you are visiting.
- A fake pop-up box from A28.pieehk.com may mislead you to download fake updates or install a piece of unwanted software. If you do as the pop-up box says, an adware or a malicious program will get the chance to infiltrate into your computer.
- Potential unwanted toolbars, banners, other malware may be added onto the computer without your consent.
- Random webpage text may be turned into hyperlinks.
- Fake updates or other software may appear on browser pop-ups.
- It may be able to record your browsing histories and collect your information according your browsing habits.
How Does A28.pieehk.com Get Inside Your Computer?
Most of the victims may wonder how A28.pieehk.com can get inside their computers without being noticed. The same as many other unwanted programs, A28.pieehk.com, the nasty browser extension, is usually added via freeware downloads from irregular websites.
Recently, it seems that "bundling" has been a very common method for the unwanted programs like adware program to invade the computer system. Therefore, to safeguard your computer from A28.pieehk.com or adware hiding in the computer, it is recommended that you should pay much attention to the download and installation of freeware. In addition, during the installation of freeware, the custom installation usually is recommended and do not select unfamiliar things easily.
Harassed by A28.pieehk.com Pop-ups? What is A28.pieehk.com?
A28.pieehk.com pop- ups, caused by an ad-supported extension for Internet Explorer, Firefox and Chrome, is distributed various monetization platforms. If you see random pop-ups keep showing up within your browsers, your PC may be attacked by an adware or a potential unwanted program. Once A28.pieehk.com manages to get inside the computer, it will automatically show up on the screen in a new browser tab, which may disturb the network users' online activities greatly and cause other trouble.
Necessary to Remove A28.pieehk.com:
As you see, A28.pieehk.com is very troublesome which will endanger your computer as well as online activities. Hence, if you are now harassed by A28.pieehk.com, it is recommended that you need to take actions to remove it from your computer without any delay.
Manual Removal Tips for A28.pieehk.com:
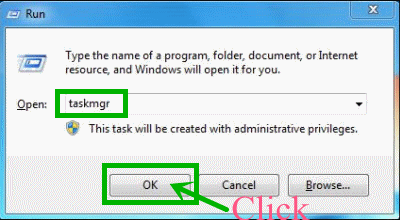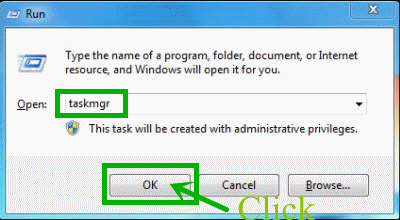
Step one: Stop all the processes related to A28.pieehk.com from task manager before removing it from the browser.
Press Alt+Ctrl+Del keys at the same time to open task manager and type taskmgr into the search blank. Then, press OK.
.png)
Step two: Remove A28.pieehk.com from web browsers
For Internet Explorer:
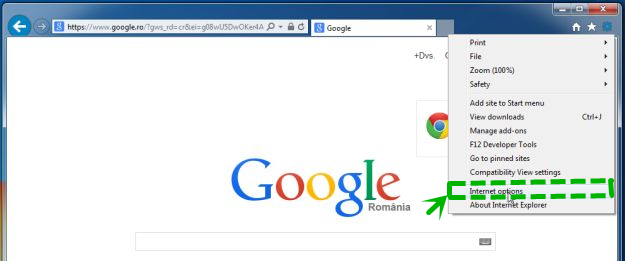
1. Reset Internet Explorer Click on the “gear icon” in the upper right part of your browser, and then click again on Internet Options.
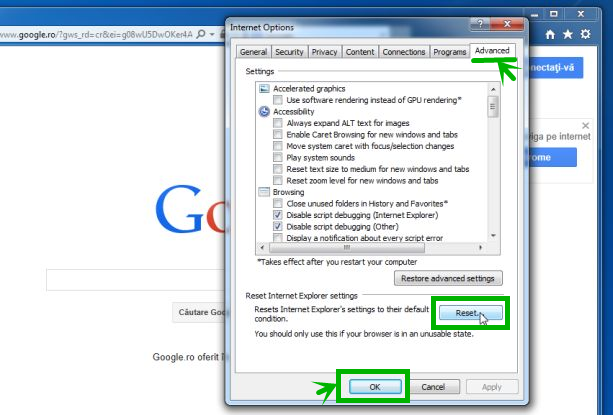
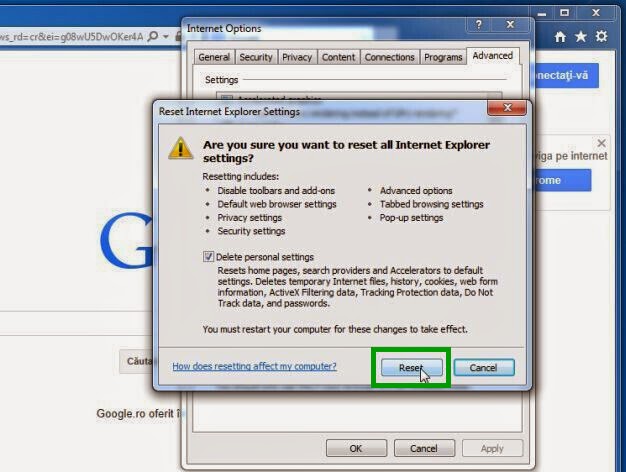
3. In the “Reset Internet Explorer settings”, select the “Delete personal settings”, then click on button “Reset”.
.jpg)
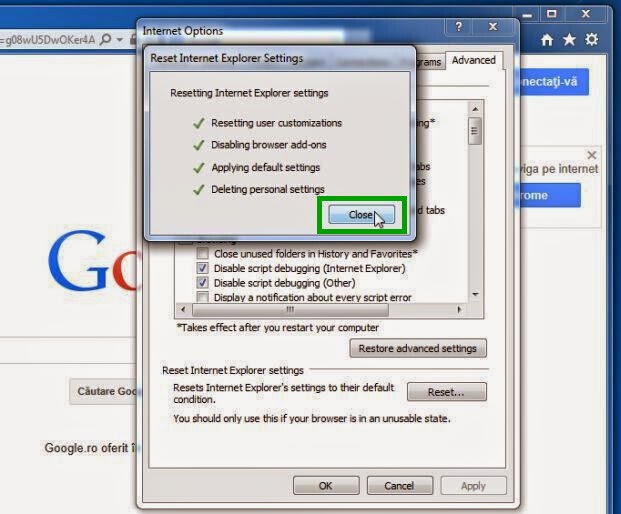
4. When Internet Explorer has completed its task, click on the button “Close”, and then you can open Internet Explorer again.
.jpg)
Step three: Using RegCure Pro to Optimize Your System After Manual Removal
As A28.pieehk.com is relatively stubborn, it is hard for certain inexperienced computer users to manually remove it completely from the system. To avoid some potential computer threats, you are suggested to download RegCure Pro to optimize your computer for good.
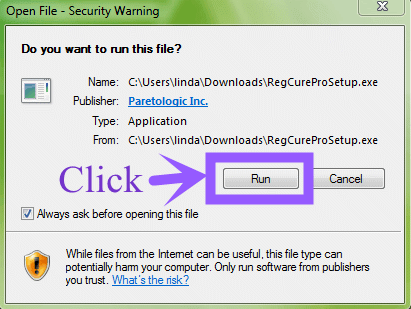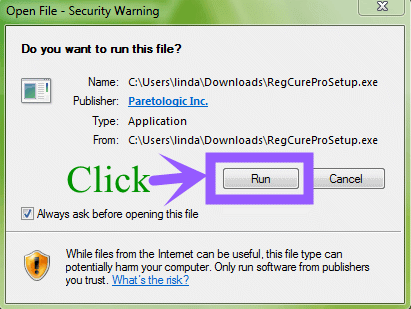
Step 1. Click the icon below to download the RegCure Pro.
Step 2. Click the button Run.
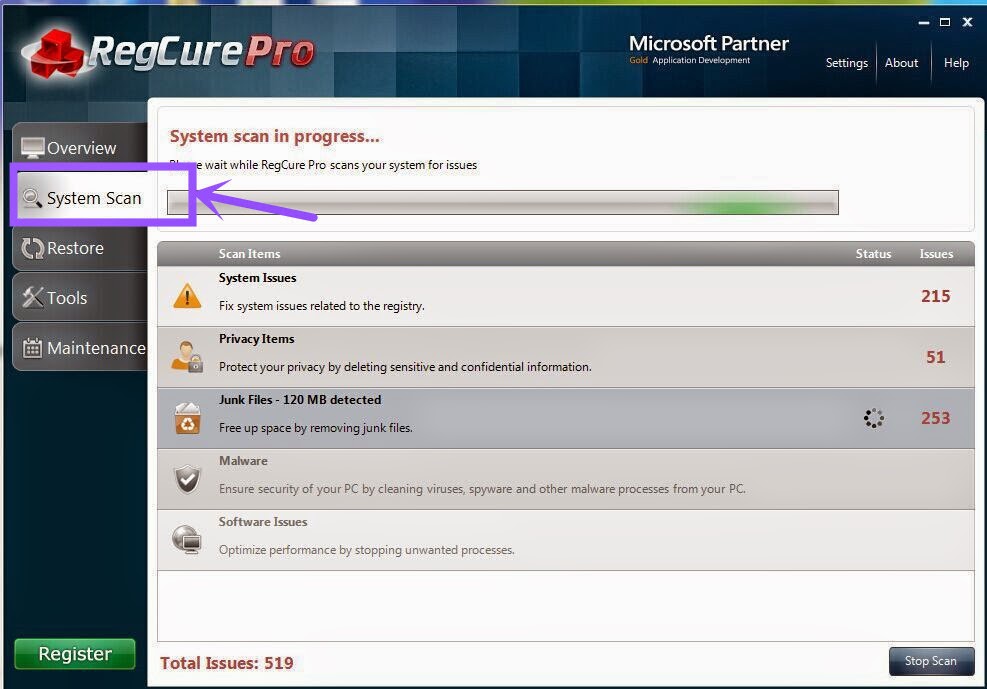
Step 3. When RegCure Pro is installed successfully on your desktop, open the RegCure Pro and it will start to scan your computer. Then, click the button Fix All to optimize your PC.

Automatically Remove A28.pieehk.com with SpyHunter
Download SpyHunter’s malware removal tool to remove the malware threats. The following steps are helpful for you to install SpyHunter.
Step1: Click the yellow icon “Download”. When you click the link, you can see the next step as following step2.
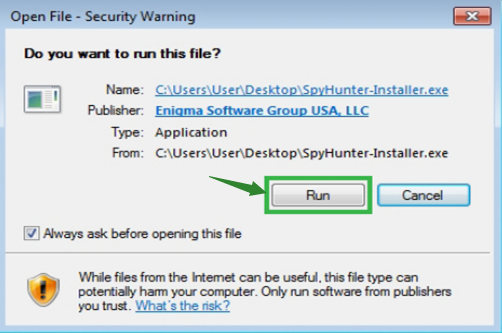.png)
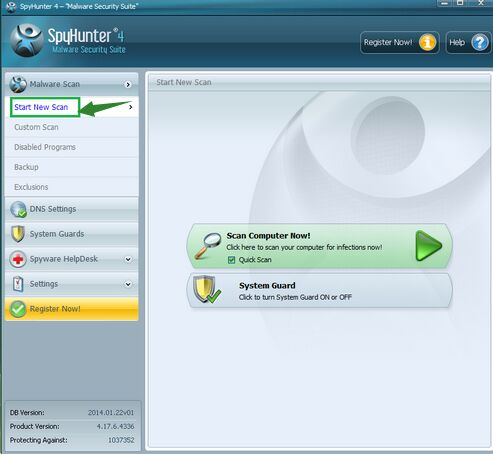
Step3: When the SpyHunter is set up successfully on your desktop, you can click the button “Start New Scan”. Thenclick the button “Select all” and “Remove” to remove the malware threats.



No comments:
Post a Comment